The growing dependence of today’s vehicles on software has transformed cybersecurity into an integral part of software engineering. With modern vehicles containing vast amounts of code, the surface for potential cyberattacks has expanded accordingly, creating new and complex attack vectors for malicious actors. This reality demands robust automotive cybersecurity engineering practices that are embedded from the earliest stages of vehicle development.
This is where the automotive cybersecurity engineering standard, ISO/SAE 21434, provides guidance on how the automotive industry approaches cybersecurity. By providing a comprehensive, risk-based framework, it guides manufacturers and suppliers to systematically identify, assess, and mitigate cyber risks throughout the entire vehicle lifecycle.
This blog post explores emerging cybersecurity risks across a vehicle’s attack surface, and how ISO/SAE 21434 sets the foundation for secure engineering.
The Modern Vehicle Cyber Risk Landscape
Connected software-defined vehicles and autonomous vehicles face particularly complex risks across multiple attack vectors.
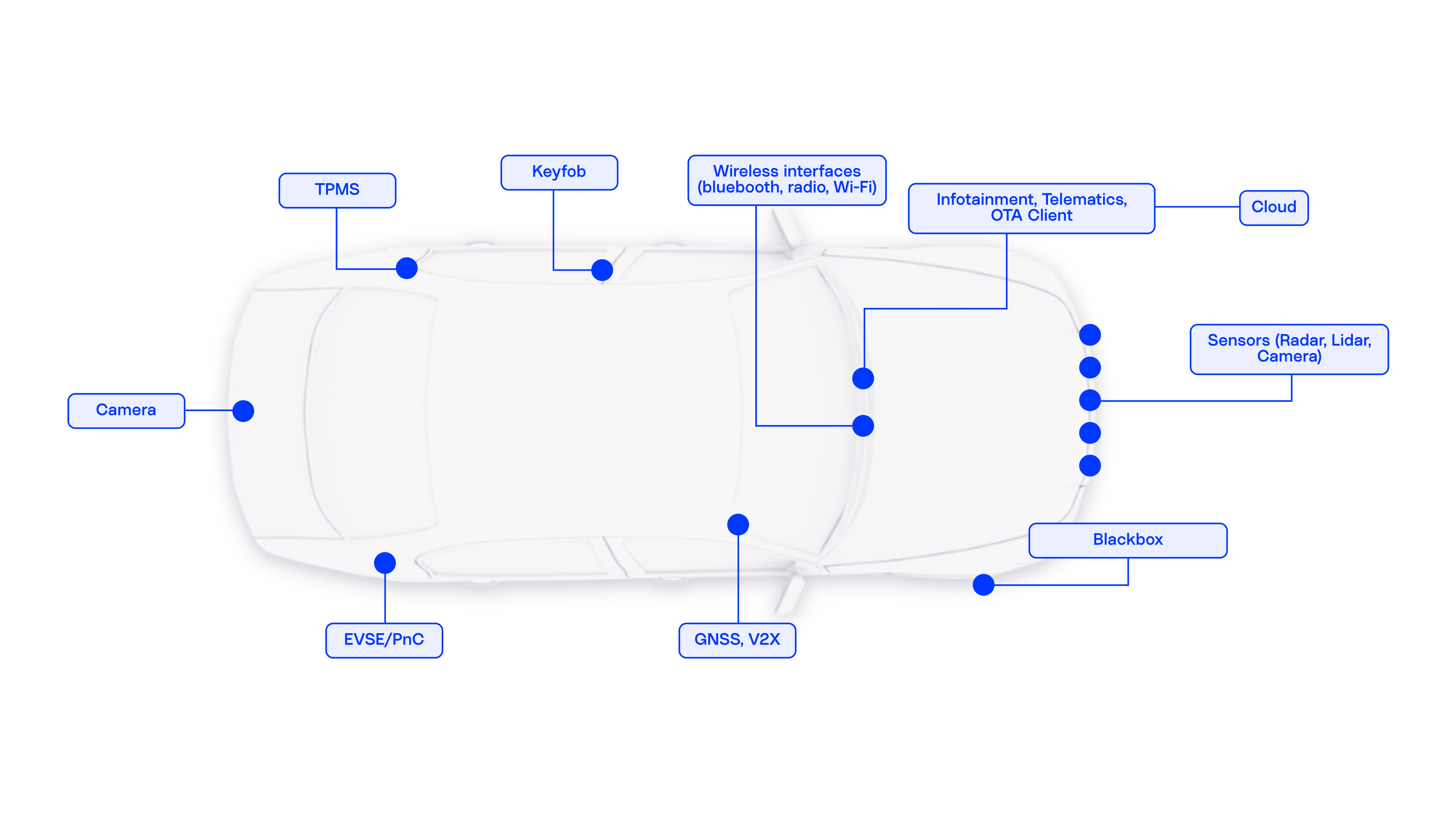
- Remote interfaces: Cellular telematics, OTA channels, Bluetooth/Wi-Fi, and V2X (vehicle-to-everything) are targets for remote code execution, man-in-the-middle (MITM), spoofing, SIM/credential theft, and backend API abuse
- In-vehicle networks: In-vehicle protocols like CAN, and Ethernet domains (e.g., SOME/IP, DoIP), face security vulnerabilities primarily due to lack of native authentication; this makes them vulnerable to attacks like message injection, replay, service discovery abuse
- Autonomy & perception: GNSS spoofing/jamming, camera/lidar blinding, adversarial ML inputs, and insecure data/model pipelines (model tampering or unsigned model packages)
- Diagnostics & manufacturing: UDS security access (seed/key) misuse, flash/reprogramming services, DoIP, leftover debug/test modes, insecure bootloaders, factory provisioning leaks, and exposed JTAG interfaces
- Supply chain: Third-party software/firmware and FOSS/OSS components, SBOM gaps, typosquatted or compromised packages, CI/CD pipeline attacks, and weak firmware-signing key custody
- Cloud & apps: Cloud backend APIs, mobile apps, and update infrastructure risks include token leakage, broken authorization, inadequate hardening, and using the cloud as a pivot into vehicle functions
Recognizing this reality raises a question: How can the automotive industry systematically address such a broad and evolving automotive threat environment? The answer lies in adopting a robust cybersecurity engineering framework like ISO/SAE 21434 and learning from Reg 155 Cyber Security Management System (CSMS) requirements.
What is the ISO/SAE 21434 Standard?
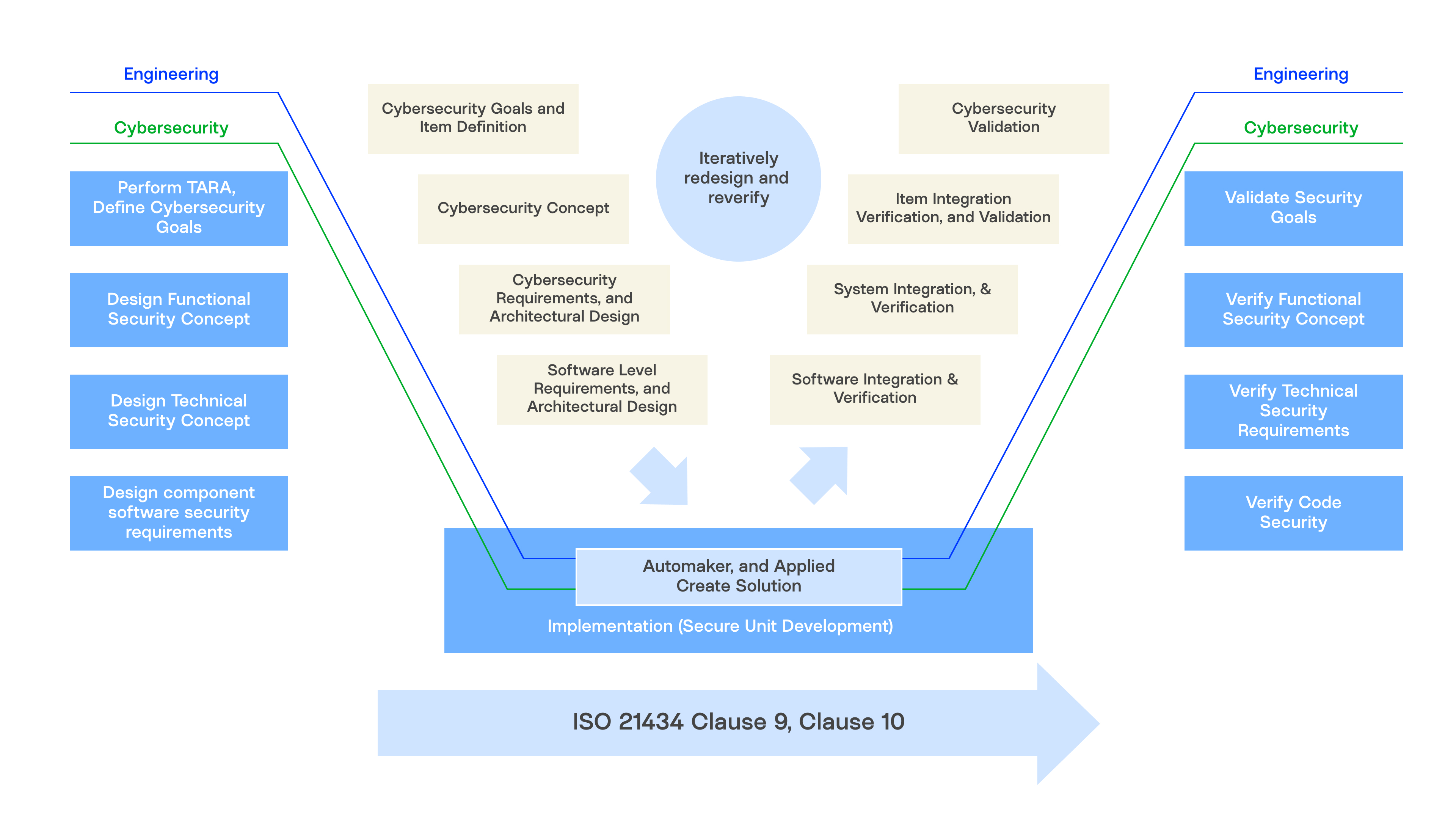
ISO/SAE 21434 defines how the OEMs, Tier 1 suppliers, and automotive software providers should engineer cybersecurity across the entire lifecycle from concept, development, production, operation/maintenance, and decommissioning.
One of the strengths of ISO/SAE 21434 is that it mandates a risk-based, multi-layered approach to vehicle cybersecurity. Our certified cybersecurity management system covers the full spectrum of these activities, confirming that we have diligently implemented security at every level. This ranges from high-level organizational practices to detailed technical analysis.
But ISO/SAE 21434 doesn’t exist in isolation. It is also the foundation for meeting automotive cybersecurity regulations like UNECE R155 and R156 and China’s GB standards.
ISO/SAE 21434’s regulatory alignment
In today’s regulatory environment, cybersecurity is more than a best practice; it's a prerequisite for market entry in EU, China, Japan, and other countries where Reg 155 is adopted.
Our ISO/SAE 21434 certified processes map directly to UN R155 CSMS criteria and support UN R156 Software Update Management System (SUMS) compliance, enabling customers to navigate approval processes across 54 UNECE markets and China’s parallel GB standards with greater speed and certainty.
Security across the vehicle lifecycle
For autonomous and modern software-defined vehicles, security vulnerabilities can have direct safety implications—not just loss of confidentiality and integrity of data. That is why our strategy is to prevent, detect, and recover with layered security controls focused on, but not limited to, cryptographic roots of trust, strong isolation, secure communications, and continuous monitoring, backed by enforced cybersecurity policies, processes, and disciplined update/incident workflows aligned to ISO/SAE 21434.
At Applied Intuition, security is integrated into every phase of our product development. Our Vehicle OS and Self-Driving system(SDS) for automotive are engineered from the ground up in line with ISO/SAE 21434 processes. With every project, we systematically conduct threat analysis, risk assessments, employ secure design practices, and perform rigorous verification and validation testing. This industry-aligned and proactive approach shifts security left and dramatically reduces the risk of the vulnerabilities in our vehicle OS and autonomy platforms.
Furthermore, by aligning with ISO/SAE 21434, we inherently fulfill CSMS-dependent requirements of UNECE Reg 155 CSMS and Reg 156 SUMS. For example, our update plans and security incident response strategies ensure that software patches are delivered under strict security controls and the integrity of vehicle software is maintained throughout each update.
Regulators increasingly recognize that an effective CSMS is the backbone of a secure SUMS, so our compliance positions OEMs for frictionless approvals wherever these regulations apply.
What This Means for Our Customers and Partners
- Faster homologation (shorter regulatory approval cycles)
- Supply chain assurance (secure integration of third‑party components)
- Lower lifecycle risk (rapid response to emerging threats)
- Future‑proof compliance alignment to Cyber Resilience Act
ISO/SAE 21434 alignment gives regulators confidence, accelerates approvals across participating markets, and supports our customers in fast-tracking cybersecurity homologation.

Driving Secure Autonomy and Vehicle Intelligence Forward
With ISO/SAE 21434 certification, Applied Intuition has reaffirmed that security is a foundational pillar of our product strategy. Our automotive software products are engineered through a rigorously managed cybersecurity process. When vehicles powered by Applied Intuition’s technology hit the road, they do so with a tangible layer of cybersecurity assurance that every reasonable measure has been taken to defend against cyber threats and protect both drivers and passengers, no matter how advanced or connected the platform.
As new mandates and standards like the EU’s Cyber Resilience Act emerge globally, we build upon our strong base to meet them head on. Early alignment with frameworks such as ISO/SAE 21434 means we can adapt rapidly, effectively future-proofing our customers’ cybersecurity homologation and market access.
The future of mobility is indeed exciting: Intelligent, autonomous, and highly connected vehicles are reshaping our roads. Yet, realizing this promise demands a shared commitment to robust cybersecurity. At Applied Intuition, we have made it our mission to be at the forefront of automotive cybersecurity innovation. By achieving and maintaining ISO/SAE 21434 certification, we deliver not only safe and secure products but also accelerate regulatory approvals worldwide.
Connect with Applied Intuition’s engineering team to learn more about our vehicle intelligence products and our alignment with ISO/SAE 21434, and how we support customers in achieving UNECE R155 compliance.
.webp)
.webp)

